@Louis_Kirsch
Tested with success. Here are my input though I think you might have already captured them in your todo list.
- password input with confirmation
- allow password reset/change
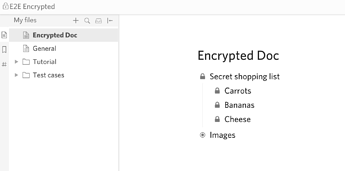
- change bullet shape to indicate Encryption status (eg from circle to diamond)
- any change (intentional/accidental deletion or insertion) made to existing encryption code string (while extension is inactive) leads to permanent “
 Could not decrypt”
Could not decrypt”